13 Must-Have Ethical Hacking Gadgets That You Can Find On Amazon
By: Adnarchist
If you’re delving into the world of ethical hacking or cybersecurity, having the right tools is essential.
Amazon offers a range of cutting-edge gadgets that cater to hackers and tech enthusiasts alike.
Below is a list of must-have hacking products available on Amazon.
1. ProMark II NFC Card Reader

The ProMark II NFC RFID card reader is a powerful device designed for testing RFID and NFC frequencies. With capabilities to copy information from RFID and NFC cards, it’s a valuable tool for those exploring the intricacies of 125 kHz, 134 kHz, and 13.56 MHz frequencies. Upgrade options, such as the Blue Shark Bluetooth 2.0, enhance its functionality, making it a versatile and efficient RFID/NFC testing device.
2. RTL SDR

The RTL SDR is a low-cost software-defined radio equipped with an RTL 2832U-based DVB-T TV tuner dongle. It allows users to pick up radio waves and listen to various frequencies. Ideal for cybersecurity professionals, it can intercept and analyze radio communications, including SMS and GSM phone calls.
3. Microcontrollers

Different microcontrollers play a crucial role in ethical hacking. The ESP8266, priced at $6, is a Wi-Fi development board suitable for creating Wi-Fi de-authors and phishing pages. The Arduino Pro Micro, though affordable, offers a great platform for various hacking experiments.
4. Bluetooth Sniffer – Adafruit Bluefruit LE Sniffer

Transform your Adafruit Bluefruit LE Friend into a Bluetooth low-energy sniffer with this special firmware image. It allows for passive data capture between two Bluetooth low-energy devices, sending the information to Wireshark for in-depth analysis. Perfect for understanding Bluetooth communication without delving into extensive specifications.
5. Hardware Key Logger

A hardware key logger is a simple yet effective tool that sits between a USB keyboard and a computer, recording every keystroke. It’s a valuable asset for cybersecurity experts, capturing up to 16 megabytes of information. Some key loggers even offer Wi-Fi or text message control, remaining undetected by traditional software.
6. Bad USB

Bad USB serves as an alternative to the USB Rubber Ducky, featuring custom hardware built around the ATmega32U4 and ESP12S. Operating via Wi-Fi, it sends keystrokes to a target computer, appearing as both a standard HID keyboard and a serial port. This device allows attackers to run interactive commands and scripts from a distance.
7. USB Killer

The USB Killer is a device designed to exploit the power supply of USB ports, quick-charging its capacitors from the USB power lines. When plugged into a device, it sends a -200 volt DC through the data lines, leading to a continuous charge-discharge cycle that renders the target device irreparable.
8. Ubertooth One

Ubertooth One is a renowned Bluetooth hacking tool, serving as an open-source 2.4 GHz wireless development platform. It allows users to monitor and develop new Bluetooth (BT) and Bluetooth Low Energy (BLE) technologies. A cost-effective alternative to commercial Bluetooth monitoring equipment, it supports various wireless technology experiments.
10. HackRF One

HackRF One is a software-defined radio (SDR) accessory capable of sending and receiving radio signals between 1 MHz and 6 GHz. It’s a versatile tool for testing and developing modern and next-generation radio technologies. Ethical hackers can leverage its capabilities to read and change radio frequencies.
11. Wi-Fi Pineapple

The Wi-Fi Pineapple, developed by Hak5, was among the first tools designed to attack Wi-Fi networks. Available in different models, the Wi-Fi Pineapple Mark 7 is known for its automatic Wi-Fi network audits. With a user-friendly web interface, it provides valuable results for testing wireless network security.
12. USB Rubber Ducky

The USB Rubber Ducky, another innovative product from Hak5, takes advantage of the HID specification to inject keystrokes into a target computer. Recognized as both a standard HID keyboard and a serial port, it allows attackers to execute pre-programmed payloads rapidly. Its versatility makes it a favorite among hackers for various payload applications.
13. Raspberry Pi 0W
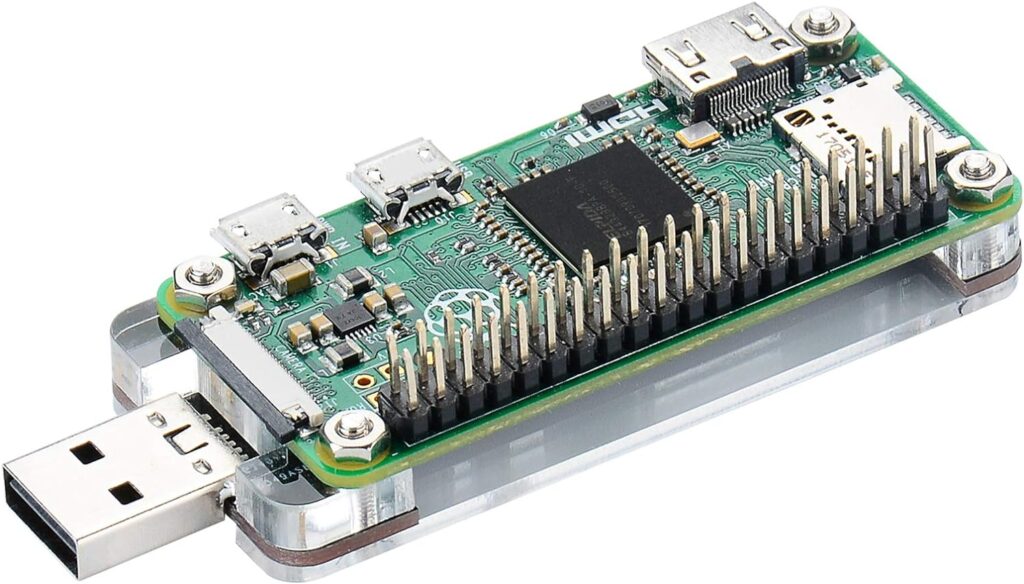
The Raspberry Pi 0W is a compact handheld computer suitable for carrying penetration testing software tools and external hardware hacking tools. With popular cybersecurity distributions like PwnPi, Kali Linux, and PwnPad available, this small device offers a portable platform for ethical hacking endeavors.
14. Raspberry Pi 4
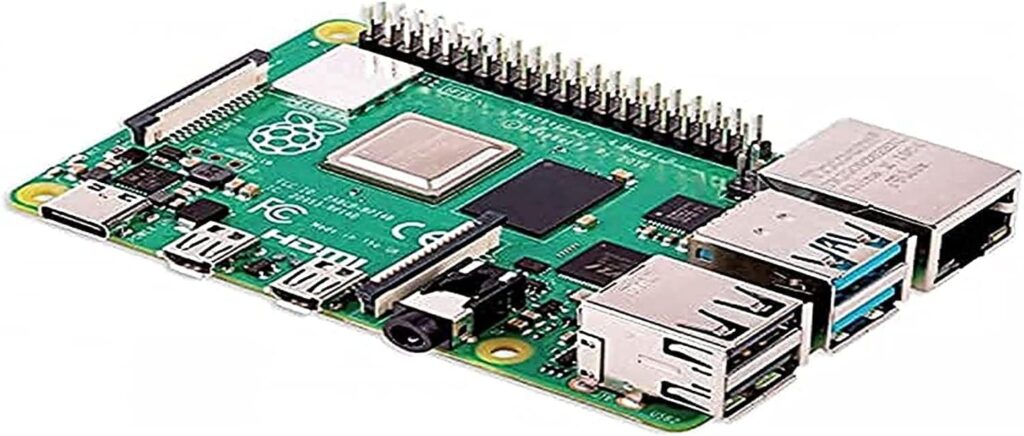
The Raspberry Pi 4, known for its popularity in the single-board computer market, is a versatile tool for cybersecurity professionals. Its credit card-sized design allows for various projects, and its ability to host a complete Linux distribution makes it a go-to device for information security and programming enthusiasts.
As you embark on your hacking journey, these Amazon gadgets provide essential tools for ethical hacking, cybersecurity, and exploration. Each product caters to different aspects of hacking, allowing you to build a comprehensive toolkit for your cybersecurity endeavors.
Related Posts
- 14 Badass Security Gadgets That’ll Keep Your Home Safe
- 10 Badass Smartphone Accessories That’ll Elevate Your Tech Game
- 17 Badass Survival Gadgets That’ll Save The Day
- Must-have reusable and portable bonfire can
- Portable off-grid smartflower solar system produces 40% more power
- Live the minimalist nomad life with this off-grid Ecocapsule
- Badass solar powered pop-up home base that makes truck life, good life